Do I Really Need A VPN (Virtual Private Network) To Stay Safe Online?
When you purchase through links on our site, we may earn a commission. Here’s how it works.

What can you do to protect your privacy and identity? Using a Virtual Private Network (VPN) service on your computer and mobile devices is a no-brainer, especially when you’re on public WiFi or traveling. For a low monthly fee and easy installation, you can protect yourself from Big Brother.
Why Do I Need A VPN Service?
A VPN service is an invisible cloak that shields your online use from virtual peeping toms. In more technical terms, a VPN service creates a secure, encrypted connection, often referred to as a tunnel, that lets you use the public internet in private.
What can a VPN do for you?
6 Features Of VPNs
- Hide you from companies tracking your data
- Keep your browsing history private
- Provide a secure WiFi connection anywhere
- Allow you to share files (torrent) anonymously
- Give you access to Netflix and your other favorite streaming services in foreign countries
- Unblock censored and restricted websites in foreign countries
How Do VPNs Work?
The internet-enabled device you use (smartphone, laptop, etc.) must have a VPN app or software loaded onto it. The VPN software connects your device to the VPN server, which encrypts your connection and secures it to help keep you anonymous online.
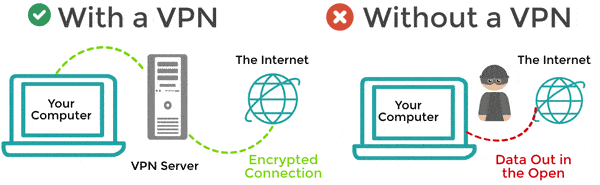
Everything you do online goes to the VPN first — from your online banking to browsing the news. Your data shows up to the internet service provider as coming from the VPN and not from your computer and location. Without a VPN, your data is out in the open, vulnerable to peeking eyes.
Using a VPN makes it so you and your computer cannot be identified easily with what you are doing online. And even if someone does see what you are doing online, your data is encrypted and not directly from you. This means your personal information, including address, credit card numbers, banking information, etc., is safer online than if you didn’t use a VPN.
Check out this video from CyberGhost to get more details about how a VPN works and the benefits you’ll enjoy from signing up.
What’s The Best VPN?
We’ve reviewed the best VPN services and ranked our top picks. Our article covers how VPNs work, and we have pros and cons for each service discussed. We also include a table to compare providers by price and features.
We’ve reviewed the top providers more thoroughly and gone in depth with pros, cons, and consumer feedback. Check out our reviews of PureVPN, CyberGhost, IPVanish, and Private Internet Access.
How Do I Set Up My VPN?
Once you’ve chosen your VPN and signed up for it, we’ll take you step-by-step through the process of how to set up a VPN on your computer (Mac or PC), smartphone (Android or iPhone), iPad, or on your home server. (Yes, we recommend you protect yourself on all your devices!)
If you decide this protection is no longer for you, we also have a guide on deleting a VPN.
Do I Need A VPN Router?
To keep all the devices in your home secure, you may want to consider a VPN Router. It’s the device that accepts internet traffic from your ISP (Internet Service Provider) and sends it to the devices in your home.
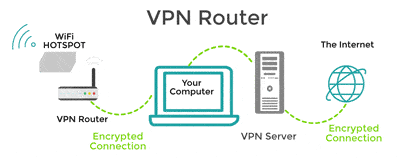
Routers come with some security features to prevent hackers from gaining access to your data, but a VPN Router is specially configured to work with your VPN for added security. It can help keep criminals out of your “digital” walls and protect your devices from Peeping Toms.
Our VPN router review includes what features your router should have, and which ones are best for gaming and other categories.
How Do I Know If I’m Protected?
We’ve had some readers ask us how to tell if the VPN is actually working — most providers have an app or service with icons indicating your level of protection. Some even offer extensive statistics, such as data sent and received while on the VPN.
The most obvious way to directly tell if you’re on a VPN is to check and see if your IP address has changed. Visit WhatIsMyIP to check before and after you connect. If you need help setting up your VPN, we have a step-by-step guide.
Are U.S.-Based VPN Providers Okay?
While shopping around for a VPN provider, you may have noticed some sites that warn against using a U.S.-based company. So, what’s the deal? Are you okay going with a company that’s headquartered in the U.S.? The short answer is yes, as long as the VPN provider has a strict no-log policy that you can trust.
Why is this even an issue? Some people are concerned about the U.S.’s involvement in the Five Eyes Alliance, the world’s leading intelligence-sharing network. So, any online activity or data passing through and stored on VPN systems headquartered in the U.S. is subject to the surveillance protocols implemented by Five Eyes. (Other Alliance members include the U.K., Canada, New Zealand, and Australia.)
VPN Terminology
Don’t understand some of the high-tech VPN lingo we’ve included in our VPN reviews? No worries! We’ve broken down all the need-to-know techie terms below.
- NAT firewall — A NAT (Network Address Translation) Firewall adds an extra layer of security by hiding computers, servers, and other IT equipment from outside threats. NAT firewalls are better than your standard OS firewalls at filtering out a lot of potential threats before you get that annoying message: Do you want to allow this connection?
- Kill switch — A VPN kill switch automatically disconnects your internet connection in case the VPN fails, gets interrupted, or you forget to enable your VPN. With a kill switch, you’ve always ensured a secure VPN connection.
- DNS leak protection — When you go to a website using your browser, it sends a request to a DNS (domain name server) with the URL that you typed in. The DNS server then points you to the correct IP address. ISPs (Internet Service Providers) assign you certain DNS servers, and they can monitor and record your online activities whenever you send a request to the server. But when you use a VPN, your DNS request should direct to an anonymous server, keeping your ISP from monitoring your connection. A DNS leak occurs when your browser inadvertently ignores your VPN connection and sends your DNS request straight to your ISP, all without your knowledge. But some VPNs come with DNS leak protection software that alerts you to that threat.
- Torrent/P2P — Torrenting or peer-to-peer (P2P) involves obtaining files and content using the Bit Torrent protocol. When you download a torrent file, you’re sharing bits of that file with anyone else who’s downloading or sharing that file. And these “peers” can see your IP address. However, if your VPN supports Torrent/P2P, you’re protected.
- Internet Protocol — Internet Protocal (IP) is the method or type of protocol by which data transfers from one computer to another computer via the Internet.
- DPI Prevention: Deep packet inspection (DPI) prevention tools allow your VPN use to be hidden and undetected, even by deep packet inspection and other firewalls that can block VPN use. DPI prevention unblocks 3rd-party app restrictions so you can gain permanent access no matter your location.
VPN Protocols
There are several VPN protocols that secure your data transport over a public network, and each protocol varies in how it keeps your data secure. Here’s a breakdown of the different protocol types.
- IP security (IPSec) uses either tunneling or transport mode to encrypt data traffic in a VPN. The transport mode encrypts only the message within the data packet (also referred to as the payload). Tunneling encrypts the entire data packet. People use IPsec, often called a “security overlay,” as a security layer for other protocols.
- Secure Sockets Layer (SSL) and Transport Layer Security (TLS) use cryptography to secure data transport over the Internet. SSL and TLS authentification require the same network parameters between remote clients and servers. With SSL and TLS, you need a certified, encrypted key to make a secure connection.
- Point-To-Point Tunneling Protocol (PPTP) uses tunneling to connect a remote client to a private server. PPTP is one of the most popular VPN protocols because its configuration and maintenance are straightforward and because it’s included with Windows. PPTP doesn’t require a key.
- Layer 2 Tunneling Protocol (L2TP) is used to tunnel data traffic between two sites. People often use L2TP with IPSec as an added security layer to keep the transfer of L2TP data packets secure. L2TP/IPSec requires a shared key or certificate.
- Internet Key Exchange version 2 (IKEv2) is a newer tunneling protocol that becomes a VPN protocol when paired with IPSec. It’s natively supported by Windows 7+, Blackberry, and iOS devices. IKEv2 is ideal for mobile devices because it’s very resilient to changing networks (i.e. moving between hotspots or switching between WiFi and mobile connections). IKEv2 is also good at automatically re-connecting VPN service if you temporarily lose your internet connection.
Will A VPN Alone Keep Me Safe?
Signing up for a VPN isn’t the only thing you’ll need to stay safe in the digital landscape we live in. We’ve written an entire article dedicated to public WiFi security tips. You can utilize these tips at the coffee shop, at your hotel when you’re traveling, at the airport, and in other public places.
Want to hear straight from the horse’s mouth about VPNs? We interview Amit Bareket, CEO and founder of SaferVPN. He tells you how to stay safe online and where he sees the future of VPNs going. You’ll also get an insight look into the company and how things work inside a VPN office.



